Access control strategies to secure health care data
June 01, 2015
By: Kurt Mueffelmann, CEO of Cryptzone
Cyber security threats, and the need to incorporate data access controls into personal and enterprise devices, plague industry worldwide. Community Health Systems, the Home Depot, JP Morgan, Sony and many others have fallen victim to sophisticated attacks that compromise sensitive information. While retail, finance and every industry in between are forced to rethink their approach to security, perhaps healthcare violations hit most intimately: they’re not just monetary, but can compromise survival. Late last year, Gizmodo reported on a study that found hospital hacks are skyrocketing because “hospitals are super easy to hack.”
Securing access—at all touch points—to personal health information remains an epidemic wreaking IT havoc on healthcare. Whether it’s the precision health movement, managed care, supply chain management, or transitioning to electronic health records, providers can’t seem to find the right antidote to secure data and restore patient confidence.
From drug and device makers, to hospitals and providers, to patients and families, the healthcare supply chain is demanding unique security approaches that disrupt traditional models of network access control, to better mitigate threats from the outside and within. These challenges are quite evident when addressing Health Insurance Portability and Accountability Act (HIPAA) compliance.
Headline-making breaches of protected health information (PHI) tell tales of astronomical numbers of medical records being accessed without permission. Besides Community Health Systems’ loss of 4.5 million patient records, Adventist Health System/Sunbelt, Bon Secours, the South Carolina Department of Health/Human Services and Anthem have also experienced major breaches. In each case, exploiting PHI was relatively easy.
Collaboration across the entire value chain can alleviate much of PHI’s risk of exploitation and ensure HIPAA compliance. Healthcare payer and provider compliance and risk managers are tasked with ensuring that vast amounts of information stays safe and is handled appropriately. How do they establish, manage and maintain an efficient access management strategy?
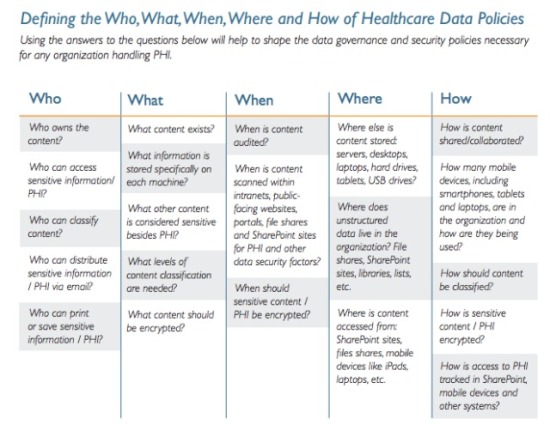
The first step is to implement healthcare data policies and compliance strategies. Using Microsoft SharePoint, a collaboration and document management platform, as an example, Cryptzone advises customers to use the following chart to develop a framework for safely handling PHI.
Once you’ve specified the PHI and policies needed to cover it—as well as any other type of sensitive and or/confidential content from structured to unstructured data throughout the organization—dynamic, identity-driven security and compliance solutions provide an answer for protection.
A Belt and Suspenders Approach to Securing PHI
When handling PHI, we suggest a belt and suspenders approach to eliminate risk. First and foremost you need to be able to collaborate on content with PHI, you just need to do so securely. Following are six steps that can be taken to ensure organizations maintain a proactive, layered and preventative risk approach.
(1) Auditing
Automated, constant information scans against policy checkpoints, and corporate policies and documents, enable organizations to assess the levels of sensitive information present and identify compliance issues. It’s also important to look at both data at rest and in motion to capture any problems in real time.
(2) Reporting
With standard and customized reports, compliance and privacy officers gain real-time insight into the status of an operating environment, can identify teams/departments where issues are recurring, and measure progress against compliance objectives over time. Reporting also calls red flags to attention, empowering developers and QA teams with the agility to target and fix issues.
(3) Classifying
Identify sensitive content, at rest or in motion, and dynamically classify the content to identify it as having a certain level of risk.
(4) Restricting
Established business rules should determine the classification of a document, as well as access to it by an individual and/or group, even if a wider audience has access to its physical location. Instituting file level permissions allow administrators to better handle multiple users. Managing file permissions is easier if they are based on the metadata values added at the time of classification.
(5) Encrypting
In addition to securing a document based on its classification, further secure highly sensitive content such as PHI by encrypting it; ensuring that only approved audiences inside or outside of the use environment can access it. In fact, the U.S. Department of Health and Human Services (HHS) dictates as part of the HIPAA Security rule that encryption must be used to protect data at rest and in motion.
(6) Tracking
The entire lifecycle of every document should be tracked, so a compliance or regulatory officer can see if and when a document has been read, emailed or printed, and by who. Recording every stop on the document’s journey is critical in the event of a breach or regulatory audit.
If you can’t show patients, upon their request, who within the organization has accessed their PHI and what they did with it, your entire healthcare supply chain is at risk. Aside from the high financial costs of breaking the law and violating rights, your healthcare institution won’t ever recover from the price of broken consumer trust.
About the author:
Kurt Mueffelmann is the president and CEO of Cryptzone. He has 20+ years of experience in the software industry, and has led HiSoftware (acquired by Cryptzone in September 2014) to steady growth since 2006 with a portfolio of industry recognized, award-winning products.
Cyber security threats, and the need to incorporate data access controls into personal and enterprise devices, plague industry worldwide. Community Health Systems, the Home Depot, JP Morgan, Sony and many others have fallen victim to sophisticated attacks that compromise sensitive information. While retail, finance and every industry in between are forced to rethink their approach to security, perhaps healthcare violations hit most intimately: they’re not just monetary, but can compromise survival. Late last year, Gizmodo reported on a study that found hospital hacks are skyrocketing because “hospitals are super easy to hack.”
Securing access—at all touch points—to personal health information remains an epidemic wreaking IT havoc on healthcare. Whether it’s the precision health movement, managed care, supply chain management, or transitioning to electronic health records, providers can’t seem to find the right antidote to secure data and restore patient confidence.
From drug and device makers, to hospitals and providers, to patients and families, the healthcare supply chain is demanding unique security approaches that disrupt traditional models of network access control, to better mitigate threats from the outside and within. These challenges are quite evident when addressing Health Insurance Portability and Accountability Act (HIPAA) compliance.
Headline-making breaches of protected health information (PHI) tell tales of astronomical numbers of medical records being accessed without permission. Besides Community Health Systems’ loss of 4.5 million patient records, Adventist Health System/Sunbelt, Bon Secours, the South Carolina Department of Health/Human Services and Anthem have also experienced major breaches. In each case, exploiting PHI was relatively easy.
Collaboration across the entire value chain can alleviate much of PHI’s risk of exploitation and ensure HIPAA compliance. Healthcare payer and provider compliance and risk managers are tasked with ensuring that vast amounts of information stays safe and is handled appropriately. How do they establish, manage and maintain an efficient access management strategy?
The first step is to implement healthcare data policies and compliance strategies. Using Microsoft SharePoint, a collaboration and document management platform, as an example, Cryptzone advises customers to use the following chart to develop a framework for safely handling PHI.
Once you’ve specified the PHI and policies needed to cover it—as well as any other type of sensitive and or/confidential content from structured to unstructured data throughout the organization—dynamic, identity-driven security and compliance solutions provide an answer for protection.
A Belt and Suspenders Approach to Securing PHI
When handling PHI, we suggest a belt and suspenders approach to eliminate risk. First and foremost you need to be able to collaborate on content with PHI, you just need to do so securely. Following are six steps that can be taken to ensure organizations maintain a proactive, layered and preventative risk approach.
(1) Auditing
Automated, constant information scans against policy checkpoints, and corporate policies and documents, enable organizations to assess the levels of sensitive information present and identify compliance issues. It’s also important to look at both data at rest and in motion to capture any problems in real time.
(2) Reporting
With standard and customized reports, compliance and privacy officers gain real-time insight into the status of an operating environment, can identify teams/departments where issues are recurring, and measure progress against compliance objectives over time. Reporting also calls red flags to attention, empowering developers and QA teams with the agility to target and fix issues.
(3) Classifying
Identify sensitive content, at rest or in motion, and dynamically classify the content to identify it as having a certain level of risk.
(4) Restricting
Established business rules should determine the classification of a document, as well as access to it by an individual and/or group, even if a wider audience has access to its physical location. Instituting file level permissions allow administrators to better handle multiple users. Managing file permissions is easier if they are based on the metadata values added at the time of classification.
(5) Encrypting
In addition to securing a document based on its classification, further secure highly sensitive content such as PHI by encrypting it; ensuring that only approved audiences inside or outside of the use environment can access it. In fact, the U.S. Department of Health and Human Services (HHS) dictates as part of the HIPAA Security rule that encryption must be used to protect data at rest and in motion.
(6) Tracking
The entire lifecycle of every document should be tracked, so a compliance or regulatory officer can see if and when a document has been read, emailed or printed, and by who. Recording every stop on the document’s journey is critical in the event of a breach or regulatory audit.
If you can’t show patients, upon their request, who within the organization has accessed their PHI and what they did with it, your entire healthcare supply chain is at risk. Aside from the high financial costs of breaking the law and violating rights, your healthcare institution won’t ever recover from the price of broken consumer trust.
About the author:
Kurt Mueffelmann is the president and CEO of Cryptzone. He has 20+ years of experience in the software industry, and has led HiSoftware (acquired by Cryptzone in September 2014) to steady growth since 2006 with a portfolio of industry recognized, award-winning products.